















Where Data Meets Humanity
Our trusted brands, fueled by AI, ignite financial clarity for the next generation. We fuse data-driven insights with human expertise, empowering the transformation of complex financial information into actionable power.

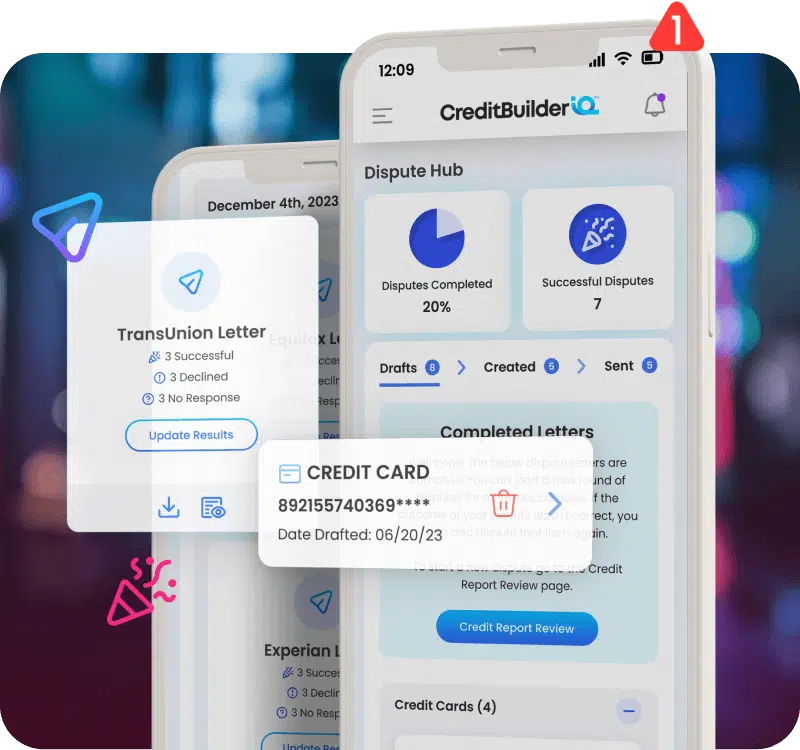
Credit Coaching & Debt Relief
Find real money solutions and effective debt relief strategies with our credit and debt education-based membership platform. Sync accounts, talk to a financial coach, and utilize Money Sensei® AI technology for personalized budgeting tips to reach financial goals.

CRM Business-in-a-Box
This all-in-one customer relationship management (CRM) tool has everything you need to power your business. This easy-to-use platform consolidates costs and effort by allowing you to connect client reports with a single click, automate daily tasks, track client progress, and more. The best part – it’s free to IDIQ partners!*
*Free to financial coaches with at least five clients with an active IDIQ brand membership.


The IDIQ Ecosystem
Craft custom solutions using our financial ecosystem to empower your business needs and drive your clients to financial success.

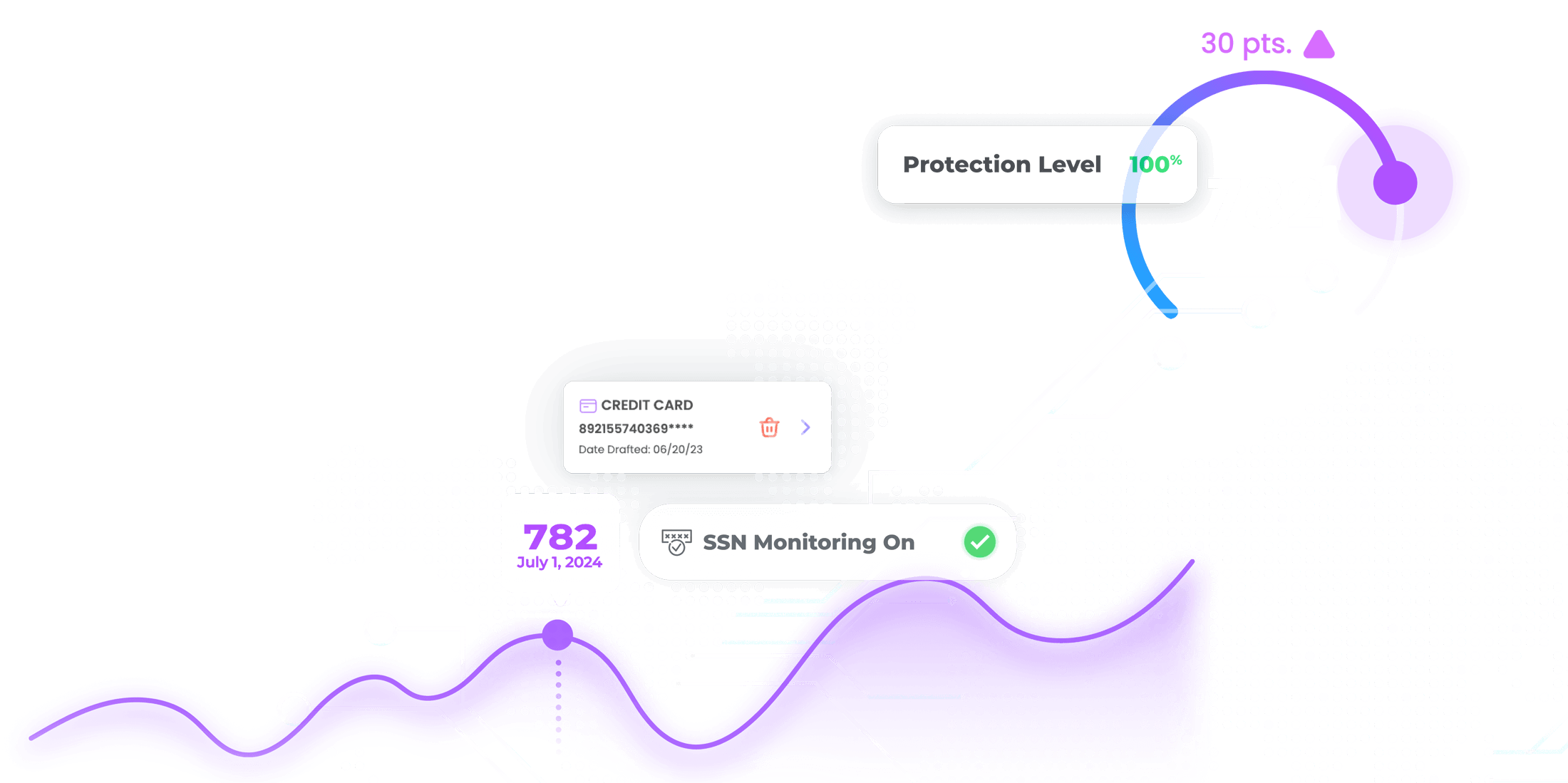
Identity Theft Protection
Safeguard your personal information with advanced monitoring and AI-powered alerts in over 35 categories.

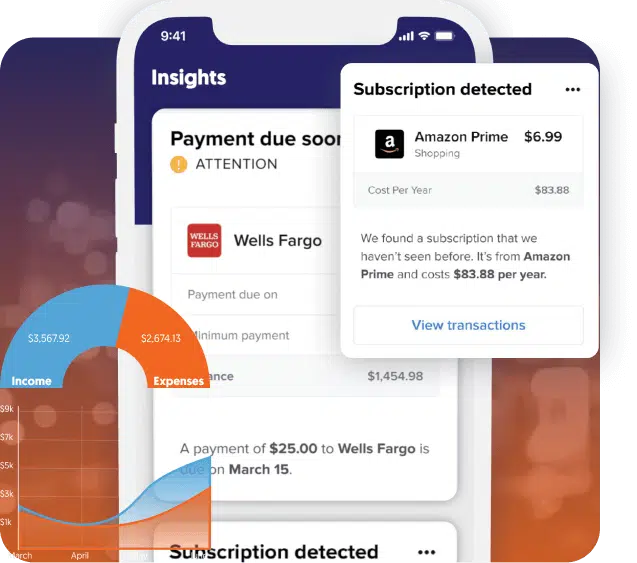
Financial Wellness
Sync your accounts, talk to a qualified financial coach, explore debt relief strategies, and more!

Credit Scores & Credit Monitoring
Real-time credit score alerts grant you control and insight into your financial future.

Legal Services
Navigate everyday legal challenges – from consultations to will preparation – for a fixed, affordable cost.

Unlock Your Growth Potential with Financial Intelligence

Decades of Broker Expertise. Benefits Revolutionized.
For decades, IDIQ has empowered brokers like you to deliver exceptional employee benefit packages. Our customizable suite goes beyond the ordinary, offering a comprehensive solution with industry-leading features such as financial wellness, identity protection, and pre-paid legal services. Streamline administration, reduce costs, and elevate your value proposition.

Retain Residents and Boost Your NOI With IDIQ.
Stop the revolving door of residents and unlock new revenue streams. Attract and keep quality tenants with resident-loved perks such as rental payment reporting, identity protection, and financial wellness programs. IDIQ minimizes your turnover costs while maximizing resident satisfaction and loyalty, leading to a healthier bottom line.

Grow Your Practice Faster with IDIQ.
In today's crowded legal landscape, IDIQ empowers firms to attract high-value clients and accelerate growth. Reach ideal clients through targeted lead generation and receive access to clients in need of a variety of services across the country. Partner with IDIQ and unlock the full potential of your legal practice.

Empower Clients. Grow Revenue.
IDIQ equips you to empower your clients on their financial journey, fostering trust and loyalty through industry-leading credit management resources. This translates to new revenue streams for you with commission opportunities. Partner with IDIQ and focus on what matters most - your clients' financial success and your company's growth.

Business Lending
Secure a competitive edge in lending with faster closings and lucrative commission opportunities.

Financial Institutions
Empower your members' financial well-being while boosting non-interest income and retention.

Advertising Partners
Tailored for content creators and online advertisers, our affiliate program can help grow your brand’s earning potential. Promote IDIQ brands on your website, blog, social media platforms, or other online space, and get paid for every qualified enrollment you send our way.
.jpeg)
IDIQ Partners with NCRA to Transform Rent Payments into Credit Building for Millions of Renters
Strategic alliance addresses critical gap for 44 million American renting households while creating new revenue and relationship opportunities for property managers
Temecula, CA, Sep. 17, 2025 – IDIQ®, a leading financial intelligence platform, today announced a strategic partnership with the National Consumer Reporting Association (NCRA) that will transform how millions of renters build credit. Through NCRA’s network of member agencies and their property management clients, renters nationwide will gain access to rent payment reporting services that will turn their largest monthly expense into a credit-building opportunity.
The partnership addresses a fundamental inequity in the credit system: while 44 million American households pay rent reliably each month, these payments traditionally provide no credit benefit, leaving renters at a disadvantage when seek loans, mortgages, or better interest rates.
“This partnership between IDIQ and the NCRA solves a massive markets problem,” said Nikki Boehle, Senior Vice President, Multi-Family Channel, at IDIQ. “Renters are already demonstrating financial responsibility through consistent rent payments. Now these payments will finally count toward building their credit history, opening doors to better financial opportunities such as access to loans and lower interest rates.”
Partnership Creates Triple Win Across Housing Ecosystem
The IDIQ-NCRA alliance delivers measurable benefits across the entire rental housing value chain:
For Renters: Monthly rent payments are securely reported to all three major credit bureaus, helping establish or strengthen credit history without taking on additional debt. Early data shows renters typically see meaningful credit score increases within months of enrollment.
For Property Managers: Rent payment reporting serves as a powerful differentiator in competitive markets while encouraging on-time payments and improving resident retention. Properties offering credit-building amenities report higher renewal rates and reduced turnover costs.
For NCRA Member Screening Companies: The partnership transforms one-time resident screening transactions into ongoing client relationships, creating new revenue streams while deepening property management partnerships.
Beyond Rent Reporting — Comprehensive Financial Wellness
This partnership extends beyond rent payment reporting to include IDIQ’s full financial intelligence suite. NCRA membership will offer residents access to IdentityIQ® for robust identity theft protection and CreditBuilderIQ℠ for personalized credit-building action plans, creating a comprehensive financial wellness platform.
This holistic approach addresses the growing demand from both renters and property managers for value-added services that support long-term resident success and retention.
“NCRA members help open doors to housing for consumers through their tenant screening services. It makes sense that we can further help those consumers once they are in their apartments through the NCRA/IDIQ partnership,” said Eric J. Ellman, President of NCRA.
Addressing Market Demand for Credit Access
The partnership comes as housing costs continue rising and credit access remains challenging for many Americans. Traditional credit building methods often require taking on debt, making rent payment reporting an attractive alternative for the millions of Americans who prioritize responsible spending over borrowing.
The service integrates seamlessly into existing property management workflows, with flexible enrollment options and automated monthly reporting to all three major credit bureaus.
For more information, visit www.IDIQ.com.
About IDIQ
IDIQ® is recognized as one of the fastest-growing industry leaders in identity theft protection and credit report monitoring. The IDIQ flagship brand, IdentityIQ®, offers real-time fraud alerts and credit report information to both protect and educate consumers. Popular IDIQ brands also include MyScoreIQ® for financial health and protection; Credit & Debt®, a credit and debt education-based membership platform; and IDIQ® Pre-Paid Legal Services℠, a leading provider of voluntary employee benefits.
The CreditBuilderIQ℠ and CreditScoreIQ℠ brands for DIY credit-building innovative tools along with the all-in-one customer relationship management tool Disco℠ round out the IDIQ full suite of products.
About National Consumer Reporting Association (NCRA)
Founded in 1992, the National Consumer Reporting Association is a national trade organization representing consumer reporting agencies and associated professionals that provide products and services to hundreds of thousands of mortgage lenders and property managers, who utilize consumer reports in their housing decisions.
Media Contact:
Kristin Hudson
Cline Public Relations
(951) 397-7595

IDIQ Report Reveals Staggering Surge in Fraud and Emerging AI Scam Tactics
Flagship IdentityIQ brand publishes report on rise of utility account fraud, student loan scams, and stolen personal documents along with rising AI threats
Temecula, California, April 3, 2025 – IDIQ®, a financial intelligence company, today released its latest Fraud Trends Report under its flagship IdentityIQ® brand, revealing alarming increases in utility account fraud, student loan scams, and stolen personal document cases over the past year.
The report, based on proprietary data, highlights an astounding 1,033% surge in utility account fraud, an almost 500% increase in student loan scams, and a 46% rise in personal document theft leading to identity theft in 2024. The report also predicts a sharp escalation in AI-driven fraud tactics, including deepfake scams, AI-powered phishing, and automated robo-scammers.
"The rapid evolution of fraud, especially with AI-enhanced scams, is a growing concern for consumers and businesses alike," said Scott Hermann, CEO of IDIQ. "We are committed to staying ahead of these threats by leveraging cutting-edge technology to protect our members and educate the public on emerging risks."
The report details key fraud trends and how AI is reshaping fraud, making scams more convincing and harder to detect. Deepfake technology is being used to impersonate individuals, AI-powered phishing is creating hyper-personalized attacks, and robo-scammers are automating large-scale fraud efforts.
"As AI technology becomes more sophisticated, scammers are finding new ways to exploit it," said Michael Scheumack, IDIQ Chief Marketing & Innovation Officer. "It’s more critical than ever for consumers to stay informed, stay on top of their credit and personal information, and take proactive security measures."
The report also outlines steps consumers can take to help avoid fraud and safeguard their personal information, including:
- Regularly monitor credit reports to detect possible suspicious activity early.
- Verify requests directly by contacting the agency or business through official communication channels.
- Be wary of urgent requests that pressure for quick action, especially those involving money transfers or sensitive data.
For more insights and information, visit IdentityIQ.com.
About IDIQ:
IDIQ® is recognized as one of the fastest-growing industry leaders in identity theft protection and credit report monitoring. The IDIQ flagship brand is IdentityIQ®, offering real-time fraud alerts and credit report information to not only protect but also educate consumers. Popular IDIQ brands also include MyScoreIQ® for financial health and protection; Credit & Debt®, a credit and debt education-based membership platform; and IDIQ® Pre-Paid Legal Services℠, a leading provider of voluntary employee benefits.
The newly-launched CreditBuilderIQ℠ and CreditScoreIQ℠ brands for DIY credit-building innovative tools along with the all-in-one customer relationship management tool Disco℠ round out the IDIQ full suite of products. To download the new report, visit https://www.identityiq.com/2024-fraud-trends-report.

IDIQ Promotes Bryan Sullivan to President & Chief Financial Officer
— Seasoned Business Leader to Lead IDIQ’s Next Phase of Growth —
Irvine, California, March 13, 2025 – IDIQ, a leader in financial intelligence, has promoted Bryan Sullivan to the new role of President & Chief Financial Officer. Sullivan, who joined IDIQ in May 2021 as Chief Operating Officer and Chief Financial Officer, has been a key player in the company’s growth and success.
In his expanded role, Sullivan will continue to report directly to Scott Hermann, IDIQ’s Chief Executive Officer. He will focus on revenue growth within existing channels, expansion into new channel opportunities and transformational operations.
“Over the last three years I am proud of the platform we have built to become the leader in financial intelligence. I am honored to step into this expanded role and further drive the strategic growth and financial success of IDIQ,” Sullivan said. “This is an exciting time of innovation and expansion. I look forward to working with our talented team to provide our members with great service and the features and benefits that protect and empower their financial lives.”
Before joining IDIQ, Sullivan served as Executive Vice President and Chief Financial Officer at loanDepot, where he played a key role in acquisitions, capital financing, and expanding the company into one of the nation’s leading consumer finance platforms. Prior to loanDepot, he had senior leadership roles at PIMCO and Goldman Sachs. Sullivan has extensive expertise in fintech, financial services, data services, and real estate services with a strong command of how to build and grow businesses.
“Bryan has been an integral part of IDIQ, demonstrating exceptional leadership, vision, and dedication to the company’s growth and success,” said Hermann, CEO of IDIQ. “I’m confident that under Bryan’s continued leadership and expanded role, IDIQ will reach new heights as the financial intelligence industry leader.”
IDIQ, founded in 2009, is one of the fastest-growing companies in America, earning five consecutive spots on the prestigious Inc. 5000 List that has also featured Microsoft, Patagonia, Intuit and Under Armour as previous list honorees.
About IDIQ:
IDIQ® is recognized as one of the fastest-growing industry leaders in identity theft protection and credit report monitoring. The IDIQ flagship brand is IdentityIQ®, offering real-time fraud alerts and credit report information to not only protect but also educate consumers. Popular IDIQ brands also include MyScoreIQ® for financial health and protection; Credit & Debt®, a credit and debt education-based membership platform; and IDIQ® Pre-Paid Legal Services℠, a leading provider of voluntary employee benefits.
The newly-launched CreditBuilderIQ℠ and CreditScoreIQ℠ brands for DIY credit-building innovative tools along with the all-in-one customer relationship management tool Disco℠ round out the IDIQ full suite of products. For more information, visit www.IDIQ.com.
Media Contact:
Kristin Hudson
Public Relations, IDIQ
951.397.7595
khudson@idiq.com
IDIQ Launches Comprehensive New Website for IdentityIQ Brand with Enhanced User Experience and Updated Features
Redesigned site for financial intelligence flagship brand also features new benefits, services, and resources to empower consumers to control and manage their financial lives
TEMECULA, CA – Jan. 9, 2025 - IDIQ®, a leader in financial intelligence, announced today the launch of the completely redesigned website for IdentityIQ®, the company’s identity and credit protection brand.
Perfectly timed to coincide with the New Year and a new focus on financial wellness, the new site has a modern look, cutting-edge tools, and was designed with an exceptional user experience in mind. The reimagined site also showcases how IdentityIQ services go beyond identity and credit protection and focuses on overall financial intelligence. Features and benefits include rent and utility payment reporting to major credit bureaus, device security, legal protection, financial management tools, and more.
“Our new website reflects our goal to empower consumers to take control of their financial lives. It represents a significant step forward in how we are connecting with our users,” said Scott Hermann, CEO of IDIQ. “We’ve reimagined every element of our site so that it’s easier than ever for users to access the tools, resources, and information they need to help safeguard their identity and credit. This redesign reaffirms our commitment to creating a seamless and user-focused journey.”
The new IdentityIQ website introduces exciting updates that include:
- Customized Consumer Journey: Purpose built to allow members to focus on financial intelligence benefits that matter most to their individual needs
- Refreshed Look: A sleek new design tailored to help users find what they need – quickly and easily
- Enhanced Product Imagery: Visually rich representations of dashboards and widgets, bringing the IdentityIQ experience to life
- Simplified Navigation: A streamlined layout that makes exploring our products and services easier than ever
- Expanded Resources & Education: News and alerts along with a comprehensive library of case studies, reports, blog articles, and more to help users make informed decisions
Visit www.IdentityIQ.com to see the redesign in action and discover how our enhanced tools and services can help you take control of your identity and credit protection.
About IDIQ
IDIQ® is recognized as one of the fastest-growing industry leaders in identity theft protection and credit report monitoring. The IDIQ flagship brand is IdentityIQ®, offering real-time fraud alerts and credit report information to not only protect but also educate consumers. Popular IDIQ brands also include MyScoreIQ® for financial health and protection; Credit & Debt®, a credit and debt education-based membership platform; and IDIQ® Pre-Paid Legal Services℠, a leading provider of voluntary employee benefits.
The newly-launched CreditBuilderIQ℠ and CreditScoreIQ℠ brands for DIY credit-building innovative tools along with the all-in-one customer relationship management tool Disco℠ round out the IDIQ full suite of products. For more information, visit www.IDIQ.com.
Media Contact:
Kristin Hudson
Public Relations, IDIQ
951.397.7595
khudson@idiq.com
What New Legislation AB 2747 Means for Property Managers

As of September 19, 2024, AB 2747 is officially in effect, requiring property managers to take prompt steps to remain compliant.
California Assembly Bill 2747 (AB 2747) introduces new requirements for rent payment reporting that directly affect property managers across the state. Understanding how this law works and how to implement it correctly is essential for maintaining compliance, supporting residents, and avoiding unnecessary operational risk.
This article explains what AB 2747 requires, key compliance deadlines, and how partnering with IDIQ can simplify rent payment reporting while creating additional value for property managers.
Key Takeaways
- AB 2747 requires property managers of buildings with 16 or more units to report positive rent payments to credit bureaus, helping residents build credit.
- Property managers must establish accurate, secure reporting systems, and notify residents by the deadlines.
- IDIQ offers integrated rent payment reporting solutions, ongoing support, and marketing materials to help property managers comply efficiently while also creating ancillary income opportunities.
What is AB 2747?
California Assembly Bill 2747 (AB 2747) expands access to rent payment reporting for California residents. Under this law, property managers of buildings with 16 or more units must offer positive rent payment reporting to credit bureaus.
When residents’ on-time rent payments are reported, those payments can appear on their credit reports, helping them establish or improve their credit scores.
AB 2747 builds on earlier legislation such as California Senate Bill 1157 (SB 1157). While SB 1157 applied to a narrower group of properties, AB 2747 significantly broadens eligibility, allowing more residents to benefit from credit-visible rent history and promoting greater financial inclusion statewide.
AB 2747 officially passed on September 19, 2024. Property managers should be preparing now to meet compliance requirements.
Key deadlines to know:
- Leases entered into on or after April 1, 2025
The offer of positive rent payment reporting must be made at lease signing and at least once annually thereafter. - Leases active as of January 1, 2025
The reporting offer must be made no later than April 1, 2025, and at least once annually thereafter. - Offers may be delivered by email or mail.
Compliance Requirements Under AB 2747
To comply with AB 2747, property managers must report positive rent payments for qualifying properties.
This includes the obligation to:
- Report rent payments: Submit residents’ positive rental payment history to credit bureaus
- Provide resident notification: Inform residents about rent payment reporting and explain how it may affect their credit.
- Ensure accuracy: Maintain precise records to prevent errors or disputes.
- Follow state reporting guidelines: Adhere to required formats, frequencies, and compliance standards.
Implementing Rent Payment Reporting Systems
Rent payment reporting can be complex, but the right systems make it manageable.
Best practices for implementation
Assess Your Current Systems:
- Review existing property management and accounting software.
- Identify gaps or upgrades needed to support compliant reporting.
Select a Rent payment reporting Partner:
- Choose a provider that integrates with your existing systems.
- Ensure reporting to all three major credit bureaus.
Implement and Train:
- Work with your provider to ensure a smooth rollout.
- Train staff on new workflows to maintain accuracy and consistency.
Communicate With Residents:
- Clearly explain how rent payment reporting works and why it benefits them.
- Provide guidance on how residents can ensure their payments are reported correctly.
💡 Want help offering rent payment reporting to your residents?
👉 Partner with IDIQ today
How IDIQ Helps Property Managers Stay Compliant
IDIQ provides turnkey rent payment reporting solutions designed to support AB 2747 compliance.
By partnering with IDIQ, property managers gain access to tools and expertise that reduce operational burden while enhancing resident outcomes.
Benefits of Rent Payment Reporting
Rent payment reporting isn’t just a compliance requirement—it delivers meaningful benefits across the board.
Benefits of Property Managers:
- Encourages on-time payments by giving residents a credit incentive.
- Reduces tenant turnover through higher satisfaction and retention.
- Enhance trust by supporting residents’ financial well-being.
⭐️ Ready to stay compliant and simplify rent payment reporting ?
👉 Partner with IDIQ today
Benefits for Residents:
- Builds credit through rent they already pay.
- Improves access to loans, credit cards, and financial opportunities.
Industry-Wide Benefits:
- Positions property managers as forward-thinking and resident focused.
- Helps organizations stay ahead of evolving legislative requirements.

Setting Up Rent Payment Reporting
Setting up rent payment reporting can seem daunting, especially without the right tools and support. Here’s a brief overview of the basics and the challenges you might face when trying to accomplish this on your own.
Understanding the Basics:
To begin with, rent payment reporting involves regularly tracking and reporting your residents' rent payments to credit bureaus.
This process requires:
- Accurate Payment Tracking: Ensuring that all rent payments are recorded accurately and on time.
- Data Security: Protecting residents' personal and payment information in compliance with data protection regulations.
- Regular Reporting: Submitting accurate and timely reports to all three major credit bureaus to reflect residents' rent payment history.
Challenges of Setting Up Rent Payment Reporting Independently:
- Technical Integration: Integrating a rent reporting system with your existing property management software can be complex and time-consuming. Ensuring compatibility and seamless data transfer is critical but often challenging.
- Regulatory Compliance: Staying compliant with AB 2747 and other relevant legislation requires staying up-to-date with changing regulations and implementing necessary adjustments. This can be overwhelming without expert guidance.
- Resource Allocation: Implementing a new system requires dedicated time, effort, and financial resources. For property managers already stretched thin, this can be a significant hurdle.
- Data Accuracy: Maintaining accurate records and ensuring no discrepancies in reporting is essential. Any errors can negatively impact residents’ credit scores and lead to disputes.
- Tenant Communication: Effectively communicating the benefits and processes of rent reporting to residents is crucial for their satisfaction.
Partnering with IDIQ streamlines AB 2747 compliance while unlocking additional operational and financial value.
With IDIQ, you get:
- Deep expertise in rent payment reporting solutions
- Continuous implementation and operational support
- High revenue-share opportunities or cost-offset options for residents
- Seamless integration with major accounting and property management platforms
- Ready-to-use marketing materials to drive resident adoption
Bottom Line
AB 2747 represents a major shift in how rent payments are reported in California. Property managers who act early can improve compliance readiness, enhance resident satisfaction, and reduce long-term operational risk.
Implementing rent payment reporting on your own can be challenging, but partnering with IDIQ makes it simple, accurate, and efficient
IDIQ rent payment reporting services integrate seamlessly with existing systems, helping you stay compliant while maximizing value for both your properties and your residents.
👉 Partner with IDIQ today to prepare for AB 2747 with confidence.
Resources:
HB 938: What You Need to Know About Missouri’s Rent Payment Reporting Bill

Missouri House Bill 938 (HB 938) is the first of many new rent payment reporting bills expected to be introduced over the coming months and years. Following in the footsteps of California’s AB 2747 legislation, this bill would require landlords to report on-time rent payments to credit bureaus.
This legislation aims to expand financial inclusion, helping renters build credit while creating benefits for landlords and property management companies. However, it also mandates changes in normal business practices that many landlords and multi-family housing managers may find overwhelming.
We worked with our in-house experts to break down the key impacts of HB 938, including what to expect, what is means for landlords and residents alike, and how you can stay compliant when this legislation goes into effect.
Key Takeaways
- HB 938 requires landlords to offer residents the ability to report positive rent payments to credit bureaus.
- Rent payment reporting can provide a pathway for residents to establish or improve credit scores.
- Rent payment reporting can benefit landlords by encouraging on-time payments and improving residents retention rates.
- Implementing rent payment reporting systems independently can be complex, but IDIQ offers seamless tools and resources to make compliance easier.
What is HB 938?
HB 938 is a legislative effort designed to promote financial inclusion by requiring landlords and property managers to report residents’ on-time rent payments to credit bureaus. The bill recognizes rent as a critical financial obligation and leverages it to help residents build stronger credit profiles. Rent payment reporting creates valuable tradelines tied to housing payments, which would otherwise be limited to homeowners with a mortgage.
Current Status of the Bill and Timeline
HB 938 was introduced by State Rep. Aaron Crossley to the Missouri House of Representatives first on Jan. 16, 2025, and read a second time on Jan. 21, 2025. The bill outlines specific deadlines for landlords and property management companies to comply and includes measures to ensure proper reporting practices. The bill has now been reintroduced as of December 1, 2025.
If passed, landlords would be required to start offering on-time rent payment reporting to all eligible residents.
The hearing for this bill has not yet been scheduled.
Compliance with HB 938
The primary requirement for compliance with HB 938 is for landlords and property management companies to offer residents the option to report positive rent payments to the credit bureaus. This entails setting up a system to accurately track and report on-time rental payments.
Some landlords may be exempt from the bill, such as landlords or buildings with fewer than 15 units, some corporate entities, and assisted housing developments. Landlords and property managers should familiarize themselves with the bill before its implementation to ensure full compliance.
Under HB 938, Landlords are Required To:
- Offer On-Time Rent Payment Reporting:
Landlords must provide residents the option to report their positive rental payment history to consumer reporting agencies. This option will need to be available for all leases starting at the specified bill implementation dates and must be offered annually. - Notify Residents:
Landlords are required to inform residents about the positive rent payment reporting option, including the process, potential benefits for credit building, and any associated fees. - Ensure Transparency and Accuracy:
Landlords must maintain accurate records of residents’ on-time rental payments and ensure any reported information is accurate to prevent disputes. - Comply with Fee Guidelines:
Any fee charged for rent payment reporting cannot exceed the lesser of $10 per month or the actual cost to the landlord. No fees can be charged if there are no associated costs for reporting.
Failure to pay the fee will not result in the eviction of the resident, nor be deducted from the security deposit; but the landlord may stop reporting rent payments after 30 days of non-payment. - Follow Regulations:
Follow any guidelines established by the state regarding the frequency and format of the reports.
Implementing Rent Reporting Systems
To comply with HB 938, landlords and property management companies may need to implement or enhance rent payment reporting systems. The following are some tips to help streamline the process.
- Evaluate Existing Systems:
- Review current property management software to determine whether it can handle positive rent payment reporting.
- Identify any upgrades or new tools needed to meet the requirements of HB 938.
- Select a Rent Payment Reporting Service:
- Choose a reliable service that integrates seamlessly with your property management software.
- Select providers that report to all three major credit bureaus to maximize credit-building benefits for residents.
- Integrate and Train Staff:
- Work with your rent payment reporting service provider to help ensure a smooth implementation.
- Train your team on the new procedures to guarantee timely and accurate reporting.
- Communicate with Residents:
- Notify residents about the positive rent payment reporting option, explaining how it works and its credit-building advantages.
- Provide clear instructions on how to opt in or out, along with answers to frequently asked questions.
- Address concerns proactively to encourage participation and foster positive relationships.
By following these steps, landlords and property management companies can not only comply with HB 938 but also support residents in building their credit histories through consistent rent payments.
💡 Want help offering rent payment reporting to your residents? Partner with IDIQ today.
IDIQ Tools and Resources Available to Assist in Compliance
IDIQ offers easily implementable, comprehensive rent payment reporting services to help property managers comply with HB 938. By partnering with IDIQ, landlords and property managers can make sure they meet all legislative requirements while enhancing the credit-building opportunities for their residents.
IDIQ simplifies rent payment reporting with:
- Integrated Reporting Tools: Easy-to-use software for landlords and property managers.
- Compliance Support: Ensures adherence to Fair Credit Reporting Act (FCRA) standards.
- Resident Communication Assistance: Pre-built materials to educate renters about rent payment reporting benefits.
- Automated Processes: Streamlines reporting to major credit bureaus.
Benefits of Rent Payment Reporting
While rent payment reporting won’t be required in Missouri until HB 938 passes, there are significant benefits to getting ahead of the competition and offering rent payment reporting now. Providing streamlined rent payment reporting provides advantages for property managers, residents, and the property management industry as a whole.
Benefits of HB 938 for Landlords and Property Managers
- Encouragement of On-Time Payments: Rent payment reporting motivates residents to pay rent on time, knowing their timely payments can positively impact their credit scores.
- Reduction in Resident Turnover: By offering residents a way to build their credit through rent payments, property managers can increase resident satisfaction and retention, potentially reducing turnover rates.
- Enhancement of Resident Satisfaction: Providing a rent payment reporting service demonstrates a commitment to residents’ financial well-being, fostering a stronger sense of community and trust.
⭐️ Partner with IDIQ today and stay compliant with easily implemented rent payment reporting and more.
Benefits of HB 938 for Renters and Residents
- Building Credit History: Can help renters establish or improve credit scores using positive rent payment data.
- Financial Empowerment: Can improve access to loans, credit cards, and better financial opportunities.
- Lower Security Deposits: Stronger credit profiles may reduce move-in costs such as security deposits.
Setting Up Rent Payment Reporting
Implementing rent payment reporting may feel overwhelming, especially without the proper tools and support. Here’s a quick look at the essentials and potential challenges you might encounter when managing this process independently.
The Basics
Rent payment reporting involves securely transmitting rental payment data to credit bureaus. This process requires accurate payment tracking, data security, resident authorization, and adherence to FCRA requirements.
Challenges of Setting Up Rent Payment Reporting Independently
Tackling rent payment reporting without streamlined software or professional support can cause a number of challenges, including:
- Administrative Burden: Tracking and reporting payments manually is time intensive and can be a drain on resources.
- Compliance Risks: Failing to meet FCRA standards can lead to penalties.
- Resident Communication: Effectively communicating to renters on rent payment reporting benefits can be challenging.
Given these challenges, partnering with a specialized service like IDIQ can simplify the process, ensuring compliance, accuracy, and efficiency.
Why Partner with IDIQ for Rent Payment Reporting
Partnering with IDIQ for rent payment reporting offers numerous benefits that streamline compliance with HB 938 and enhance your property management operations.
Expertise in Rent Reporting Solutions
IDIQ brings extensive experience in rent reporting solutions, helping you meet all the requirements of HB 938 effortlessly. Our expertise helps you navigate the complexities of the legislation, providing peace of mind and allowing you to focus on managing your properties.
Professional Support
IDIQ provides continuous support throughout the implementation process. From initial setup to ongoing management, our team is dedicated to helping you succeed. We offer training, resources, and personalized assistance to ensure your rent reporting system operates smoothly.
Commitment to Helping Property Managers Achieve HB 938 Compliance
We aim to help you maximize the benefits of rent reporting, enhancing tenant satisfaction and retention while positioning your properties as attractive options for responsible renters.
Financial Benefits & Ancillary Income Opportunity
IDIQ can offer the highest revenue share to property management company partners. Alternatively, you have the option to forgo commission and reduce the cost of a plan for your residents, providing flexibility in how you wish to structure your partnership
Additionally, implementing rent payment reporting with IDIQ can lead to increased revenue through improved tenant retention and satisfaction. Residents who see tangible benefits in their credit scores are more likely to renew leases, reducing turnover costs and vacancies.
Compatibility with Major Accounting Platforms
IDIQ rent payment reporting solutions are designed to integrate seamlessly with major property management and accounting software platforms, helping ensure smooth implementation and minimal disruption to your existing processes.
Ease of Implementation
Our solutions are user-friendly and require minimal effort from your on-site teams. IDIQ handles the heavy lifting, allowing your staff to focus on their core responsibilities.
Marketing Collateral Provided by IDIQ
IDIQ provides marketing materials to help you communicate the benefits of rent reporting to your residents, enhancing enrollment rates and resident satisfaction.
Empowering Renters and Landlords: HB 938’s Lasting Impact
HB 938 marks a significant step toward financial inclusion in the Missouri rental market. By making rent reporting mandatory, the bill empowers renters to build credit while helping landlords and property management companies improve resident relationships and encourage timely rent payments.
Partnering with IDIQ helps ensure that both parties maximize the benefits of this groundbreaking legislation with seamless integration.
IDIQ offers comprehensive rent payment reporting services that seamlessly integrate with existing systems, ensuring compliance with HB 938 while maximizing benefits for property managers and residents. Our solutions not only help you meet regulatory requirements but also enhance operational efficiency, resident satisfaction, and financial outcomes.
Don’t wait until the last minute to start preparing. Partner with IDIQ today to ensure your property management practices are compliant, efficient, and beneficial to your residents.
Meet the author Nikki Boehle.
Rent and Utility Reporting: Alternative Tradelines are the Fastest Credit-Building Win Your Clients Aren’t Using (Yet)

If you work with borrowers on credit readiness, you’ve seen the same pattern over and over again.
A client pays rent on time for years. They pay utilities on time. Their cash flow is stable. But their credit file does not reflect that consistency in a meaningful way.
When a credit file is thin, missing positive history can be the difference between “almost there” and “not yet.”
For credit education professionals and mortgage and lending teams, this is a structural problem, not a behavioral one. Clients do the right things, but credit systems do not always capture them.
That gap is exactly why alternative tradelines are moving from niche to mainstream.
In October 2022, the Federal Housing Finance Agency (FHFA) validated two newer credit score models: VantageScore 4.0 and FICO 10T. These models are designed to incorporate additional data sources, including rent payment history, as part of a broader view of borrower behavior.
This shift creates a practical opportunity: a high-impact, low-friction way to help clients show credit-visible progress sooner, while strengthening your own business through better retention and engagement.
This guide covers:
- What “alternative tradelines" really means for client credit strategy in 2026
- Why VantageScore 4.0 and FICO 10T make this more relevant now
- Where rent and utility reporting fits in a credit improvement plan
- How to position it with clients as speed-to-impact, not a gimmick
- How to operationalize this inside a full credit improvement plan
- How IDIQ turns this into a growth lever for your practice
What are Alternative Tradelines, Really?
Alternative tradelines are payment accounts that can show up on a person’s credit report but are not “traditional” credit products like credit cards, auto loans, student loans, or mortgages.
These reflect recurring bills people already pay, rather than borrowed money.
What counts as an alternative tradeline
- Rental payments: On-time rent payments are reported to one or more credit bureaus.
- Utility payments: Electricity, gas, water, and phone
- Telecom services: Cell phone, landline, internet, and cable bills.
Why these Tradelines are Becoming More Important Now
For years, alternative tradelines lingered on the sidelines of credit conversations. Helpful in niche cases, but not central to score strategy.
That is changing.
FHFA’s validation of VantageScore 4.0 and FICO Score 10T signals a clear direction for the industry: a fuller view of borrower behavior over time.
Credit evaluation is moving toward more complete representations of financial behavior and rent, and utility history is part of that conversation. That makes rent and utility reporting a “do-now” lever.
It gives clients something tangible they can do immediately while longer-cycle strategies take effect. It also gives credit professionals something concrete to track early on: on-time payments turning into credit-visible history while the rest of the plan works in the background.
Rent Reporting: a Speed-to-Impact Lever for Thin-File Clients
The appeal of rent payment reporting is straightforward:
- Your client already pays rent, which is likely their largest monthly expense
- You aren’t asking them to open a new line of credit
- You are converting existing behavior into a reported, positive payment history
In a recent report from the Credit Builders Alliance (CBA), adding a positive rent tradeline has moved the needle significantly. Nearly 79% of participants experienced an increase in their credit score, with an average jump of 23 points.
Renters who started with no credit score became scorable. Subprime renters saw the biggest movement, averaging an increase of 32 points.
The takeaway? Rent reporting can add consistent on-time history to files that are light on positives, which is where early progress can be the hardest to generate.
Utility Reporting: Where it Can Help, and Setting Expectations with Your Clients
Utility bill payments don’t typically affect credit scores because most utility companies do not report on-time payments to credit bureaus.
This creates an opportunity: if a client has consistent, on-time utility payments, utility payment reporting can add additional positive payment evidence.
There are two important points to communicate to your clients clearly:
- Utility reporting may add positive history, but results vary by credit profile and scoring model.
- Not all “utility and credit” approaches are the same. Some report as tradelines, some add data to a single bureau, and some do not affect credit reports at all.
How to Position Rent and Utility Reporting with Clients
Some clients assume rent and utilities already “count.” Others worry that reporting sounds like a shortcut. Your job is to frame both as credit visibility, clarify the differences between them, and set clean expectations up front.
- Start with a simple definition
- “This takes bills you already pay, like rent and utilities, and helps that on-time history show up as credit-visible payment information. This can strengthen your file over time without adding new debt.”
- Clarify the difference between rent and utilities
- “Rent reporting is usually the primary lever because rent is typically your largest monthly payment and can add consistent on-time history.”
- “Utility reporting can be a secondary layer. Utilities do not typically show up as positive history by default, so reporting can add additional proof of stability.”
- Clarify what rent and utility reporting is not
- “This is not a promise of a specific score change, and it does not replace credit building fundamentals like on-time payments, utilization, and correcting errors.”
- “It also does not affect every scoring model or every lending decision the same way, even when the payment history appears on your credit file.”
Use language that feels responsible, not promotional- “We’re helping your credit file reflect what you’re already doing well.”
- “This is credit visibility, not a shortcut.”
- Avoid phrases that can backfire
- “This will raise your score fast.”
- “This works for everyone.”
- “This changes what lenders see immediately.”
Credit wins for clients become retention wins for your business
One of the biggest challenges in credit education and lending workflows isn’t client understanding - it’s follow-through.
Offering rent and utility reporting helps close that gap by giving clients tools they can use immediately.
This approach allows you to:
- Turn education into action: Clients are more likely to stick with a plan when there is a clear “do this next” step that is easy to implement.
- Create a consistent check-in cadence: Credit monitoring and reporting gives you structure for follow-ups, progress reviews, and early risk detection.
- Differentiate your workflow: Most professionals can explain utilization and payment history. Fewer can operationalize momentum for their clients.
There is also a simple reason this tends to improve follow-through: people want help, and they want their responsible payments to count.
According to an IDIQ study, 95% of renters say they want access to resources that help them build and manage credit, and 80% want on-time rent payments factored into credit scoring.
When clients are already motivated, the most helpful thing you can do is make the next step clear, realistic, and easy to act on.
How rent and utility reporting fit into a full credit improvement plan
Rent and utility reporting work best as a supporting layer inside a structured plan, not a one-and-done trick.
A practical way to run it: confirm, activate, and reinforce.
Confirm: Before recommending rent and utility reporting, make sure the results are clean and consistent.
- Confirm rent and utility payments are paid on time, every time
- Set expectations: this builds payment history over time, not overnight
- Use compliance-friendly language: “credit-visible proof” instead of “guaranteed score increase”
Activate: Use reporting where it has the highest chance of impact.
- Prioritize thin-file, low-history, or previously unscorable clients
- Lead with rent reporting as the primary signal, with utility reporting where it makes sense
- Introduce reporting during slower phases of a plan to maintain momentum
Reinforce: Keep it from becoming “set it and forget it.”
- Position rent reporting as a way to get credit for the biggest bill they already pay
- Layer in utilities as an extra positive signal when appropriate
- Repeat the core message clients actually remember: “We’re helping your on-time bills show up where lenders can see them
What You Can Deliver Through IDIQ
Rent and utility reporting only helps your business if clients implement it correctly. IDIQ can help.
With IdentityIQ solutions, you can give your clients access to:
- Rent reporting to help clients build credit-visible payment history from their largest monthly bill
- Utility reporting as an additional positive layer when appropriate
- 3-bureau credit reports and scores, plus 24/7 credit monitoring to track what posts and spot changes early
- Identity theft protection, including $1 million in identity theft insurance
- Credit education tools to reinforce fundamentals and improve follow-through
- If you want rent and utility reporting to actually work as a retention lever, this is the missing piece: it needs to be easy to implement, easy for clients to understand, and easy for you to operationalize alongside monitoring and score tools
Final Notes
When clients are doing everything right, but their credit still looks thin, rent and utility reporting can help their file catch up to their behavior.
It’s not magic. It’s visibility.
Unleash better credit outcomes for your clients and accelerate your business growth. Partner with IDIQ to unlock credit reports and monitoring, score tools, identity protection, and rent and utility reporting.
IDIQ is a financial wellness company. IDIQ does not provide legal advice. The information on the website is not legal advice and should not be used as such.
Tax Season = Scam Season: How to Protect Clients and Build Loyalty in 2026

Tax season creates a perfect storm for fraud.
Your clients are gathering W2s, 1099s, Social Security numbers, employer details, and banking information. They’re logging into accounts they rarely touch. They’re moving quickly because they want their refund.
And scammers are waiting to capitalize.
In 2024, the FTC received more than 1.1 million identity theft reports, and consumers reported more than $12.5 billion in fraud losses overall.
The risk is not just coming from complex cyberattacks. It often starts with seemingly innocent touchpoints: a text, a link, a “refund” message that looks official. In 2024 alone, consumers reported losing $470 million to scams that started with text messages.
When one bad click can cost a refund, rack up new accounts, and trigger months of cleanup, tax season becomes your moment to add protection, not just guidance.
In this article, you’ll discover:
- Why tax season is a high-risk time for identity theft and refund fraud
- A simple client action plan you can share
- The most common red flags clients should watch for
- What happens if your client is impacted
- How to use tax season to deepen relationships and drive revenue
Why Tax Season is High-Risk in 2026
Tax season creates the conditions criminals look for: a mass exchange of sensitive personal information, moving quickly across email, portals, mail, and third-party preparers.
Clients are uploading documents, responding to refund status updates, and trying to stay on deadline. Scammers try to insert themselves into that workflow.
Two patterns matter most right now:
- Refund-themed messages are a common entry point: The FTC warned in January 2026 that texts or emails claiming a refund is “processed” or “approved” often push people to click a link and enter SSNs and banking details.
- Digital impersonation spikes during filing season: The IRS warns about phishing and smishing and emphasizes that it does not make initial contact through email or social media channels.
The key takeaway is simple.
During the tax season, the risk feels real. Clients are paying attention - that makes this a natural moment to talk about protection.
A Simple Tax-Season Safety Plan for Your Clients
It helps to give your clients a clear baseline for what “safe behavior” looks like during tax season.
Encourage clients to:
- Use official refund tracking tools only: Refund status should be checked through IRS-approved resources like “Where’s My Refund?” or the IRS2go app.
- Be cautious with refund messages: Unsolicited texts or emails asking for identity or banking information should be treated as suspicious until verified through official channels.
- Set up an IRS Identity Protection PIN: An IP PIN helps prevent someone else from filing a tax return using a client’s Social Security number.
- Choose tax preparers carefully: The IRS warns against preparers who refuse to sign returns, promise unusually large refunds, or base fees on refund size.
- Secure rarely used accounts: Updating passwords and enabling multi-factor authentication is especially important for tax, payroll, and financial accounts used only once a year.
- Add credit file protection when appropriate: Fraud alerts and credit monitoring can help catch identity misuse early if tax information is compromised.
With these basics in place, clients are better prepared to spot problems before damage spreads.
Related: IDIQ Partners IDIQ Partners with Three National Tax Associations
The Most Common Tax Season Scams Clients Fall For
Tax scams aren’t always obvious. Many look-like routine financial messages or even helpful advice.
Educating your clients on the most common patterns can help them pause and verify before handing over the information needed to file a fraudulent return or steal a refund.
“Refund approved” texts and emails
These messages claim a refund is waiting and pushing the receiver to click a link to verify their identity or banking information. The FTC specifically warned about this pattern in 2026.
IRS impersonation texts or calls
Scammers pose as the IRS, using urgency, fear, and threats to push action. They may promise a “too good to be true” refund, threaten that clients must pay now or face arrest or deportation, or provide fraudulent website links that take users to harmful websites instead of IRS.gov.
Social media “refund hacks” and bad advice
Social media can be one of the most overlooked tax season risk areas, because it doesn’t look like a scam at first. It can look like financial advice, posted confidently, shared by someone who seems credible.
But bad tax advice on social media can mislead taxpayers about their credit or refund ability. In some cases, these posts are doing more than spreading misinformation; they may route taxpayers towards links that connect them directly with cybercriminals.
Tax Refund Advance Scams
Some scams exploit confusion around refund advances. Criminals steal a taxpayer’s personal information, impersonate them, and file a fraudulent return through a tax preparation service. That service then approves a refund advance based on the fake return, and the scammer routes the advance to their own accounts.
By the time anyone realizes what happened, the scammer is long gone - and taxpayers have lost refund money AND must repay the loan taken out in their name.
If your client gets hit, the worst outcome is not just the stolen refund. It’s the follow-on fraud that spreads into credit, banking, and future filings.
Related: Protecting Your Clients in the Age of Evolving Fraud
What To Do If Your Client Is Impacted by Tax Scams
This is a high-stress moment for clients. Your job is not to diagnose a tax issue. Your role is to create a clear sequence of next steps, reduce panic, and help protect their credit file from follow-on fraud.
Recommended next steps include:
- Have your client create an official identity theft report: Recommend they report the incident at IdentityTheft.gov or call the FTC. This creates documentation and a recovery plan they can follow.
- Have your client contact the IRS identity theft unit: Recommend they contact the IRS for identity theft assistance so the IRS can help address tax-account risk and identity verification steps. The IRS specifically directs identity theft victims to specialized assistance at 800-908-4490.
- If needed, file IRS Form 14039: If your client cannot e-file because a return was already filed under their SSN, IRS guidance is to file a paper return and include Form 14039.
- Protect against follow-on fraud: Tax fraud often leads to broader identity theft issues. Credit monitoring and fraud alerts help detect new activity.
- Close the loop on financial accounts: Recommend your client contact any banks and financial institutions where their accounts may be at risk, especially if the tax refund scam involved their banking details or logins.
How You Can Use Tax Season To Deepen Relationships And Drive Revenue
Tax season provides credit professionals a natural reason to check in. When protection is the focus, your outreach will feel helpful, not promotional.
Check In Proactively
Here’s a sample client message you can share:
“Subject: A quick tax-season safety reminder
Tax season is a common time for refunds and identity scams. Before you file, here are a few reminders to help protect your information:
- Use official IRS tools to check your refund
- Ignore messages asking you to click links or share personal details
- Consider setting up an IRS Identity Protection PIN
- Let me know if anything looks unusual
If you would like, we can also do a short tax-season protection review check to walk through these steps together.”
Offer a Tax Season Protection Review
A quick check-in can make all the difference. Plan time to meet with clients, providing a structured time to help them identify risks and recommend the right next steps.
Discussion items:
- Create an IP PIN plan, explaining why it matters and how to get it
- Review the top refund scam patterns they should avoid
- Scan for credit red flags: new accounts, unexpected inquiries, or address changes
- Share official refund tracking resources
Offer add-ons that inspire confidence
Credit professionals can keep support simple while still giving clients meaningful protection. One of the easiest ways to do that is to offer optional add-ons powered by IDIQ, so clients can choose the level of coverage that fits their situation.
By partnering with IDIQ, you can offer clients:
- Credit monitoring: Help clients stay aware of changes that may signal follow-on fraud, including new accounts, inquiries, or suspicious activity.
- Identity theft protection: Give clients added coverage during a season when personal data is moving fast and scams are most active.
- Family protection monitoring: Extend protection beyond the primary filer, which can matter when households share devices, documents, and financial accounts.
- Identity restoration support: Provide guided help if identity theft occurs, so clients aren’t left trying to navigate recovery steps alone.
Because tax season creates urgency and real vulnerability, clients are often more receptive to protection offerings during this window, especially when they are positioned as a practical layer of support.
Final Thoughts
Tax season is a high-risk season. Your clients are moving sensitive data quickly, and scammers are waiting to take advantage.
If you want to build loyalty in 2026, treat this time as a client protection program: a short review, a simple checklist, and a clear offer for monitoring and support.
For partners who want to turn this into a repeatable client program, IDIQ makes it easier to deliver protection at scale.
With IdentityIQ tools, partners can pair education with action, offering identity theft protection, fraud alerts, three-bureau credit monitoring, plus credit reports and score tools that help clients stay informed and protected throughout tax season and beyond.
IDIQ is a financial wellness company. IDIQ does not provide legal advice. The information on the website is not legal advice and should not be used as such.